Cyber Security ISO 27001
ISO 27001:2013 Cyber Security
The foremost aim of the formulation of cybersecurity standards is to improve the security of IT infrastructure and IT products used in organizations.
Cyber Essentials
Cyber Essentials against the most common cyber-attacks by showing them how to implement basic security controls. Cyber Essentials is a good first step towards demonstrating that your organisation takes cyber security seriously.
The scheme’s certification process is designed to help organisations of any size prove their commitment to cyber security while keeping the approach simple and the costs low. .
Cyber Essentials covers four key areas of cyber security: .
1) Boundary firewalls and Internet gateways.
2) Secure configuration.
3) User access control.
4) Malware protection.
Cyber security is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It's also known as information technology security or electronic information security. The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
Network security is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
.Application security focuses on keeping software and devices free of threats. A compromised application could provide access to the data its designed to protect. Successful security begins in the design stage, well before a program or device is deployed. .
Information security protects the integrity and privacy of data, both in storage and in transit. .
Operational security includes the processes and decisions for handling and protecting data assets. The permissions users have when accessing a network and the procedures that determine how and where data may be stored or shared all fall under this umbrella.
.Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data. Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event. Business continuity is the plan the organization falls back on while trying to operate without certain resources. .
End-user education addresses the most unpredictable cyber-security factor: people. Anyone can accidentally introduce a virus to an otherwise secure system by failing to follow good security practices. Teaching users to delete suspicious email attachments, not plug in unidentified USB drives, and various other important lessons is vital for the security of any organization.
The ISO 27001 standard is also structured to be compatible with other management systems standards, such as ISO 9001 and it is technology and vendor neutral, which means it is completely independent of any IT platform.
Any organization that holds sensitive information is a candidate for ISO 27001 certification. In particular, companies in the healthcare, finance, public, and IT sectors can benefit greatly from a certified ISMS. This standard will help your company coordinate all your security efforts both electronically and physically, coherently, cost effectively and with consistency and prove to potential customers that you take the security of their personal / business information seriously.
ISO 27001:2013 Model:
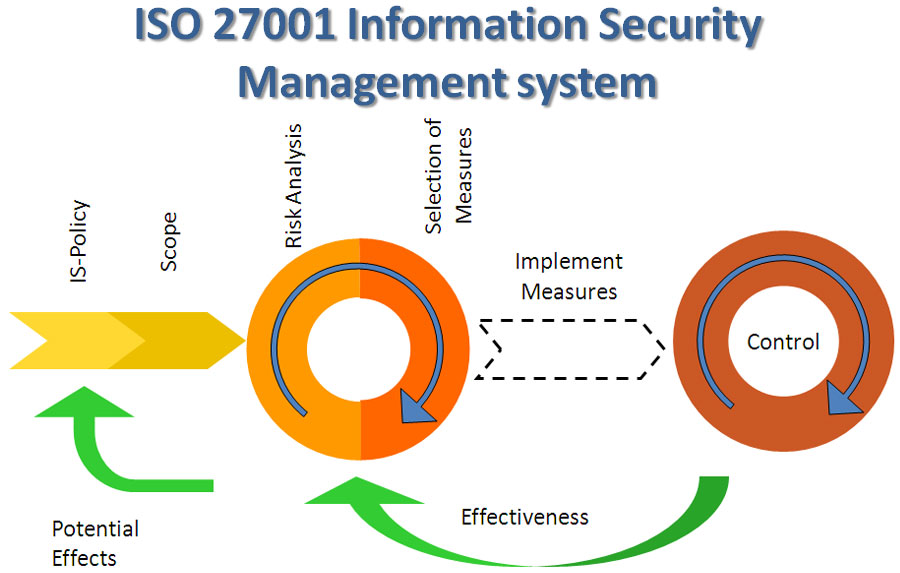
Any organization can benefit from implementing ISO 27001
ISO 27001 sets out how an organisation should approach its information security management project and specifies the essential components. Recognised internationally, achieving certification provides credibility for those claiming their client information is secure.
- Customer focused organization.
- Reduces and prevents information security risks.
- Increased reliability and security of systems and information..
- Improved customer and business partner confidence.
- Identify risks and put controls in place to manage or reduce them.
- Gain stakeholder and customer trust that their data is protected.
- Improved management processes and integration with corporate risk strategies.
- Continuous improvement.
ISMS
Our services are essential for businesses of all types whether it is to get products to market, meet contractual and regulatory requirements or improve quality, safety, efficiency and sustainability./p>
The Benefits of ISO 27001:2013:
ISO ISMS Certification helps in:
- Customer satisfaction. Deliver products that consistently meet customer requirements.
- Reduced operating costs. Continual improvement of processes and resulting operational efficiencies mean money saved.
- Improved stakeholder relationships. Improve the perception of your organization with staff, customers and suppliers.
- Improved risk management. Gain a greater understanding of organizational risks; focus on consistency and traceability of products to help prevent problems.
- Proven business credentials. Independent verification against recognized standards speaks volumes.
- The owner of a registered mark is entitled to a presumption of mark ownership and exclusive use since the application filing date.
- Open doors to win more business. Procurement specifications often require certification as a prerequisite for suppliers.








